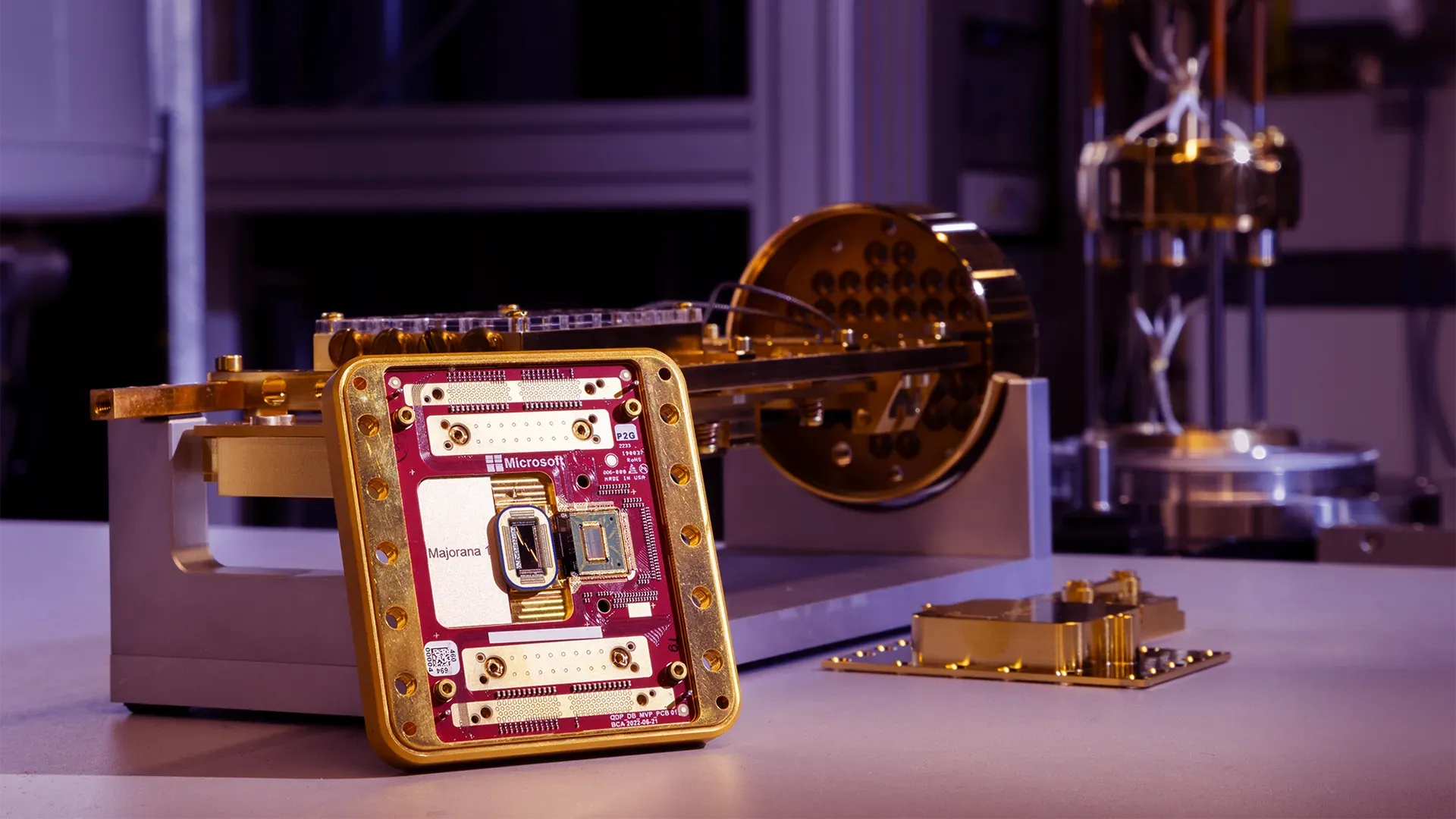
Encryption and Quantum Computing - Fighting the Big Crunch of 2025
The growing importance of online security requires that we pay close attention to protecting the personal information we share over the internet. Encryption is the most common way to safeguard data, transforming readable information into a form that cannot be understood without special knowledge. But the development of quantum computing threatens to outpace today's encryption methods. As a futurist, this worries me and I think we should prepare ourselves for the Big Crunch.
Researchers in China have recently claimed to have found a way to break the most common form of online encryption using quantum computers with just 372 qubits, a significant turning point in the field of computer security. With experts predicting that quantum computing will become powerful enough to break existing encryption by 2025, which I'd like to call the Big Crunch of 2025, we must prepare for the future by exploring new encryption methods that can withstand the quantum threat.
This article will examine the world of encryption and quantum computing. We will delve into the potential impact of these technologies and discuss possible solutions to looming security threats.
Analysis of the Big Crunch of 2025

The term Big Crunch is not commonly used in the context of encryption and quantum computing. Instead, it is a cosmological theory about the universe's ultimate fate. The theory suggests that the expansion of the universe will eventually slow down and reverse, leading to the collapse of the universe in a massive gravitational collapse, often referred to as the Big Crunch.
With that said, for the purposes of this article, we will use this metaphorically to describe the potentially catastrophic consequences of a breakthrough in quantum computing on current encryption methods. So, as we approach 2025, the threatening Big Crunch has become a topic of great concern among experts in various fields.
In this section, we will explore the various theories and models proposed to explain the Big Crunch and analyse the potential consequences of this event. A comprehensive examination of the available evidence aims to provide a clear and insightful understanding of the Big Crunch and its implications for our future.
Comparing the Threat: Big Crunch vs. Y2K Bug
The Big Crunch is a phenomenon predicted to occur when the world's computing capacity exceeds its ability to process data, resulting in a catastrophic collapse of the global digital infrastructure. Many have compared the Big Crunch and the infamous Y2K bug that plagued the world's computer systems at the turn of the millennium. While the Y2K bug was a serious threat requiring significant attention and resources, the Big Crunch might represent an even greater risk.
The Y2K bug was primarily a technical issue that could be addressed through updates to software and hardware. In contrast, the Big Crunch is a fundamental challenge to the very foundations of our digital infrastructure. It requires a more comprehensive approach, involving technical solutions, strategic planning, risk management, and a rethinking of our approach to data and information.
Before we move on, it is crucial to consider that the concept of a Big Crunch occurring in 2025 or any other specific date is not scientifically supported. However, if we were to consider a hypothetical scenario where such an event could occur, the consequences for organisations could be catastrophic.
The collapse of the digital infrastructure due to a Big Crunch could result in the loss of critical data and damage to infrastructure, leading to severe disruption of operations and supply chains. In today's highly interconnected and digitised world, organisations rely heavily on their IT infrastructure to store and process data, communicate with customers and suppliers, and operate essential systems such as finance, logistics, and production. Therefore, a digital infrastructure collapse could have far-reaching consequences for businesses, governments, and society.
Moreover, the Big Crunch could also result in significant financial losses and reputational damage for organisations. A sudden collapse of the digital infrastructure, with all data suddenly becoming easily accessible to anyone with a powerful enough quantum computer, could result in the loss of valuable intellectual property, sensitive customer information, and trade secrets, exposing organisations to legal liabilities and regulatory fines. The reputational damage resulting from such an event could also lead to a loss of customer trust and a decline in market share, ultimately impacting the long-term sustainability of an organisation.
Organisations need to take a proactive approach to identify potential vulnerabilities in their IT infrastructure, develop robust contingency plans, and prepare for the post-quantum world to mitigate the risks of such an event. This includes investing in redundancy and backup systems, developing disaster recovery plans, and implementing robust cybersecurity measures by incorporating quantum-resistant encryption across all their systems. Organisations should also develop contingency plans for their supply chains, including identifying alternative suppliers and diversifying their operations geographically to minimise the impact of a disruption.
While the Y2K bug was a significant challenge for the world's computer systems, the Big Crunch presents a much more significant threat to our digital infrastructure. Organisations that take a proactive and comprehensive approach to the issue will be better positioned to mitigate the risks and emerge from this challenge stronger and more resilient than before.
The Role of Security Analysts and Organisations

The Big Crunch serves as a reminder that the threat landscape is continuously evolving, and organisations must be prepared to adapt and respond to new risks.
In today's world, where data is the lifeblood of organisations, the topic of security is of paramount importance. With the increase in cyber attacks, organisations are becoming more conscious of the need for better security measures to safeguard their data. Security breaches are estimated to cost the world $10 trillion by 2025.
The Big Crunch of 2025 as an imminent threat is an event that security analysts and organisations cannot ignore. For security analysts, it is, therefore, crucial to understand the potential impact of the Big Crunch on the security landscape and the business.
As this event approaches rapidly, staying ahead of the curve is vital by identifying potential vulnerabilities in existing security systems and developing strategies to mitigate the risks. This requires identifying the IT systems and data sources most at risk of being breached and decrypted by a quantum computer and what to do when it happens. Of course, the best approach to avoid the Big Crunch of your organisation is to incorporate quantum-resistant encryption across all your systems, but more on that later.
Security analysts and organisations must work together to protect their data from this impending threat. Failure to take proactive measures to safeguard data could have serious consequences, both financially and in terms of reputation. For this reason, it is of utmost importance for security analysts and organisations to stay prepared for the upcoming Big Crunch.
Digital Security and Privacy in a Post-Big Crunch Era

If it were to happen, the big crunch of 2025 would not be just a one-time event with short-term implications. Its effects would continue reverberating throughout the digital security and privacy landscape for years. It is essential for security analysts and organisations to understand these long-term implications to prepare for the future.
The primary concern is the impact that encryption has on secure communications. Yes, this also includes your embarrassing WhatsApp messages! The Big Crunch will render current encryption methods useless, leaving organisations vulnerable to cyber-attacks and individuals at risk for malware, blackmailing and other threats. This would require a complete overhaul of encryption systems and a shift towards quantum-safe encryption methods.
A second concern stems from the possibility that government surveillance may negatively affect individual privacy. As governments scramble to protect themselves from the chaos of the Big Crunch, they may implement more invasive surveillance measures, infringing on individuals' privacy rights. It will be crucial for organisations to navigate these changes and ensure they are complying with any new regulations while still protecting their customers' data.
The Big Crunch may also accelerate the adoption of new technologies such as blockchain and decentralised systems. These technologies offer unique security and privacy benefits, and their adoption may increase as organisations seek to protect their data in the aftermath of the big crunch. However, only a few blockchains incorporate quantum-resistant encryption, and it is not Bitcoin or Ethereum...
The Big Crunch of 2025 could have far-reaching implications for digital security and privacy. Eventually, the Big Crunch may fundamentally shift how we think about digital security and privacy. As we confront the reality that even the most advanced encryption methods can be rendered useless, we may need to rethink our entire approach to security. This could mean a move towards more decentralised, distributed systems or a greater emphasis on physical security measures.
Unravelling the Relevance of Quantum Computing

As we have discussed previously, quantum computing is a powerful technology with the potential to revolutionise many areas of computing, including digital security. Understanding quantum computing and its relevance is critical in developing effective strategies for securing digital assets against the threat of the Big Crunch in 2025.
Quantum computing differs from classical computing in that it relies on quantum bits, or qubits, which can exist in multiple states simultaneously, rather than classical bits, which can only exist in a 0 or 1 state. This allows quantum computers to perform certain computations exponentially faster than classical computers, making them a formidable threat to existing cryptographic methods.
The relevance of quantum computing to digital security lies in its ability to break many of the commonly used encryption algorithms, including RSA and elliptic curve cryptography. This is because these algorithms are based on the difficulty of factoring large numbers, which is a problem that can be solved quickly by a quantum computer using Shor's algorithm.
However, quantum computing is not just a threat to digital security; it also has the potential to be a powerful tool for improving security. Quantum cryptography, for example, relies on the principles of quantum mechanics to provide unbreakable encryption. Quantum cryptography allows people to detect attempts to intercept or eavesdrop on communications, making it an ideal solution for secure communication in the age of quantum computing.
Understanding quantum computing and its relevance to digital security is critical in developing strategies for protecting sensitive information against the threat of the Big Crunch in 2025. As the technology continues to evolve, we will likely see new threats and opportunities arise, making it essential for security professionals to stay up-to-date on the latest developments in quantum computing and its implications for digital security.
Challenges to Current Data Encryption: The Quantum Threat

With quantum computers' increased power and efficiency, traditional encryption methods may no longer be sufficient to protect sensitive data. As a result, it is becoming increasingly imperative for organisations to prepare for the quantum computing era and adopt new quantum-resistant encryption methods that can withstand the challenges posed by this emerging technology.
In this section, we will delve deeper into the potential consequences of quantum computing on data encryption and explore the steps organisations can take to mitigate these risks.
Quantum Computing's Breaking Power on Current Data Encryption Methods
As of now, quantum computing is a rapidly advancing field that poses great opportunities and challenges for the security of our digital data. Quantum computing threatens data encryption, which relies on the computational complexity of factoring large numbers. The factoring problem is the basis of many encryption methods that are widely used today, such as RSA encryption.
RSA encryption is widely considered secure as long as the key length is long enough, which makes factoring the product of two large prime numbers computationally infeasible for classical computers. However, quantum computers can solve the factoring problem much faster than classical computers using a specific algorithm known as Shor's algorithm.
Shor's algorithm uses quantum parallelism and quantum interference to factor large numbers in polynomial time, making many currently used encryption methods vulnerable to attacks by quantum computers. This includes RSA encryption and other encryption methods, such as Elliptic Curve Cryptography (ECC) and Digital Signature Algorithm (DSA), which rely on the same mathematical problem.
Quantum computing has the potential to break current data encryption methods because it can solve complex mathematical problems much faster than traditional computers. This means that the encryption keys used to protect our sensitive data, such as bank transactions, medical records, or your embarrassing WhatsApp messages, could be easily decoded by a quantum computer, making the information vulnerable to theft or misuse. To ensure the security of our data in the future, researchers are exploring new encryption methods resistant to quantum computing attacks, with four quantum-resistant cryptographic algorithms now selected.
Quantum-resistant encryption is a form of cryptography that can resist attacks from classical and quantum computers. Unlike traditional cryptographic methods, which rely on mathematical problems that are difficult for classical computers to solve, quantum-resistant cryptography is based on mathematical problems that are believed to be difficult for quantum computers to solve as well.
The challenge in developing quantum-resistant cryptography is that it needs to be compatible with existing infrastructure and technology. This means that any new cryptographic methods must be integrated seamlessly into current systems without causing disruption or significant changes. Also, the fact that quantum-resistant cryptography is still in its early stages of development, and there has yet to be a widely accepted standard for these methods, makes it difficult for organisations to determine which quantum-resistant cryptographic methods are most effective and secure.
That said, the need for quantum-resistant cryptography is clear. As quantum computing technology advances and becomes more powerful, so does its ability to break into our digital data. Researchers and organisations must work together to develop new resilient encryption methods against quantum computing. As such, organisations must begin preparing for the transition to post-quantum cryptography to protect their data against quantum computing attacks. This should not start tomorrow, but today as there is no time to waste.
Industries Most Vulnerable to Quantum Computing Threats

The potential impact of the Big Crunch of 2025 is far-reaching and could have significant implications for a wide range of industries. However, some sectors are more vulnerable than others. Here we will explore the potential risks and consequences of the Big Crunch on the finance, healthcare, and government industries.
Finance
The financial industry is among the most data-intensive and interconnected industries, relying heavily on secure and accurate data processing.
The finance industry is highly reliant on secure data transmission and storage, making it particularly vulnerable to the threat of the Big Crunch. The potential consequences of a breach could be severe, including financial losses, reputational damage, and even the collapse of entire financial systems. Without secure encryption, transactions and personal data could be easily accessed and manipulated, leading to chaos in the financial markets.
Financial institutions must, therefore, adopt quantum-resistant encryption algorithms to protect their sensitive data. And they must do so as soon as possible.
Healthcare
The healthcare industry is another highly sensitive and data-intensive industry, with vast amounts of patient data that must be kept secure and confidential.
As such, the healthcare industry is another sector at high risk of being impacted by the Big Crunch. With the increasing use of electronic medical records and connected medical devices, personal health data is more vulnerable than ever. The consequences of a data breach in this industry could be catastrophic, including identity theft, medical fraud, blackmailing and even loss of lives if medical devices are compromised.
Hospitals and other healthcare providers should convert to quantum-resistant encryption algorithms to secure patient data.
Government
Government agencies and institutions hold vast amounts of sensitive and confidential data, making them a prime target for cyber-attacks. Aside from that, many government agencies rely on legacy systems that are vulnerable to cyber attacks already, making them even more susceptible to data breaches.
The potential consequences of a successful attack during the Big Crunch could be significant, including damage to national security, loss of public trust, and even threats to public safety. Without secure encryption, hackers could easily access and manipulate this sensitive information, causing widespread chaos, disruption and even war.
Ultimately, the finance, healthcare, and government industries are among the most at risk of being impacted by the Big Crunch of 2025 due to their heavy reliance on sensitive data and the potentially catastrophic consequences of a data breach. These sectors must take proactive steps to strengthen their cybersecurity defences and adopt quantum-resistant encryption methods to mitigate a data breach's potential risks and consequences. Failure to do so could result in significant financial losses, reputational damage, and even threats to public safety.
Effective Strategies to Mitigate the Risks of the Big Crunch

As the Big Crunch of 2025 looms on the horizon, organisations must prepare themselves for the potential consequences of this event. While it might be impossible to prevent the Big Crunch from occurring at any given time, some steps can be taken to mitigate the risks and minimise the impact. The following are some ways organisations can prepare for and respond to the challenges posed by the Big Crunch and how they can ensure the security of their data and systems in the face of this impending threat.
Exploring Potential Solutions: Advancements in Quantum-Resistant Encryption Methods
The first solution is, of course, the development and implementation of post-quantum encryption algorithms, which are designed to be resistant to attacks from quantum computers. As mentioned, these algorithms use mathematical problems believed to be difficult for quantum computers to solve, providing a new level of protection for sensitive data. Some examples of post-quantum encryption methods include lattice-based cryptography, code-based cryptography, and hash-based cryptography.
Avoiding the consequences of the Big Crunch could also be possible by implementing quantum key distribution (QKD) systems. QKD is a method of securely distributing cryptographic keys over a distance using quantum communication protocols. It leverages the principles of quantum mechanics to ensure that any attempt to intercept the keys will be detected, making it impossible for an attacker to access the encrypted data and allowing for secure communication.
Amongst the benefits of QKD, it provides a future-proof solution to secure communication. Even if an attacker has access to a powerful quantum computer, QKD will still be secure as it is based on the fundamental laws of physics. However, one of the limitations of QKD is that it requires specialised hardware and infrastructure to implement, making it a costly solution for many organisations.
Nevertheless, QKD can be an effective solution for organisations that require the highest level of security and privacy, such as government agencies, financial institutions, and healthcare organisations. Through effective implementation of QKD systems, these organisations can protect their sensitive data and communications from the threat of the Big Crunch and any other emerging threats in the future.
Furthermore, organisations need to implement a multi-layered approach to cybersecurity, including encryption, access controls, network security, and employee training. Also, regularly updating and patching systems and performing regular security audits can help identify vulnerabilities and minimise the risk of a breach.
While there is no single solution to this complex problem, the development of quantum-resistant encryption methods, along with a comprehensive approach to cybersecurity on an ongoing basis, can help mitigate the risks and ensure that sensitive data remains secure.
Advancements in Developing Quantum-Resistant Encryption Methods

There are ongoing efforts to develop post-quantum cryptographic standards that organisations and governments can adopt. These standards will provide guidelines and requirements for implementing quantum-resistant encryption methods, ensuring that the encryption systems used in various applications are secure and resilient to quantum attacks.
Many researchers and experts, including academics, industry experts, and government agencies, collaborate on this issue. For example, the National Institute of Standards and Technology (NIST) has been running a public competition since 2016 to encourage the development of post-quantum cryptographic standards. This competition is ongoing, with the final round of evaluations expected to be completed in 2024 and four algorithms already selected, as mentioned earlier.
While there is still much work to be done regarding quantum-resistant encryption, other efforts are also going on in the face of the looming threat of quantum computing. Various initiatives have been launched to address these issues and develop effective solutions.
The National Quantum Initiative Act is one example of such an initiative, which was signed into law by the United States government in 2018. This act provides funding and resources for the development of quantum computing technology and the research and development of quantum-resistant encryption methods. Other countries, such as China and the European Union, also invest in quantum technology research.
The U.S. government has allocated substantial funding towards quantum research and development, including the National Quantum Initiative Act, which provides $1.2 billion in funding over five years. The European Union has also committed €1 billion to the development of quantum technologies as part of its Quantum Flagship program.
At an international level, the International Organization for Standardization (ISO) and the NIST are working on developing quantum-resistant cryptographic standards. These standards will provide guidelines for encryption methods that can withstand attacks from quantum computers.
In addition to these initiatives, there is growing collaboration between governments and the private sector to address the challenges of quantum computing. This includes partnerships between tech companies and government agencies to develop quantum-resistant encryption methods and to implement security measures to protect against potential attacks.
Also, the Global Forum on Cybersecurity Expertise (GFCE) has established a working group to address quantum computing and its impact on cryptography. This group comprises representatives from various countries and organisations and is focused on developing guidance and best practices for mitigating the risks of quantum computing.
The government and international response to the risks posed by quantum computing and data encryption has been encouraging. With continued investment in research and development and collaboration between different stakeholders, effective solutions can be developed to mitigate the risks and ensure the security and privacy of sensitive information in the digital age. However, once this work is done, and the quantum-resistant encryption, standards, and regulations are in place, the hard work will start: ensuring that all organisations worldwide will implement quantum-resistant encryption, the standards and the regulations. A daunting task that almost seems impossible to be completed on time for the Big Crunch of 2025.
Final Thoughts
The Big Crunch of 2025 represents a significant threat to digital security and privacy, as current data encryption methods are vulnerable to quantum computing attacks. While this threat may seem daunting, there are steps that organisations can take to mitigate the risks, including investing in quantum-resistant encryption methods, updating their systems and software regularly, and fostering a culture of cybersecurity awareness.
The potential consequences of the Big Crunch are dire, particularly for industries such as finance, healthcare, and government. These organisations must proactively protect themselves and their customers' data. Governments and international organisations are also taking notice of the threat posed by quantum computing and working to develop new standards and regulations to address these issues.
To conclude, progress is being made toward quantum-resistant encryption methods, and while there is still much work to be done, there is a reason for optimism. By staying informed and proactive in our approach to digital security, we can help ensure that the Big Crunch of 2025 does not become a digital catastrophe.
Images: Midjourney